In an international drive via technology, protecting records has in no way been more critical.On the same time as information protection and cybersecurity are modern day enforced, they play a crucial characteristic in safeguarding sensitive facts from theft, misuse, and damage. As cyber threats increase more those concepts and their significance is vital to staying relaxed in the virtual age.
Understanding Information Security and Cybersecurity
Facts security and cybersecurity are frequently pressured, but they’re no longer exactly the same. Records protection is the wider idea that guarantees the confidentiality, integrity, and availability of all sorts of facts, whether or not virtual or bodily. It covers encryption, endpoint security, and even physical measures to maintain data secure. Cybersecurity, alternatively, is a branch of records safety that focuses in particular on shielding virtual structures, networks, and gadgets from cyber threats. In today’s related international—wherein communication, purchasing, transportation, healthcare, and amusement all depend upon computers and the internet—each is vital to safeguarding the huge amounts of touchy facts saved across structures and gadgets.
Why Cybersecurity matters more Than Ever
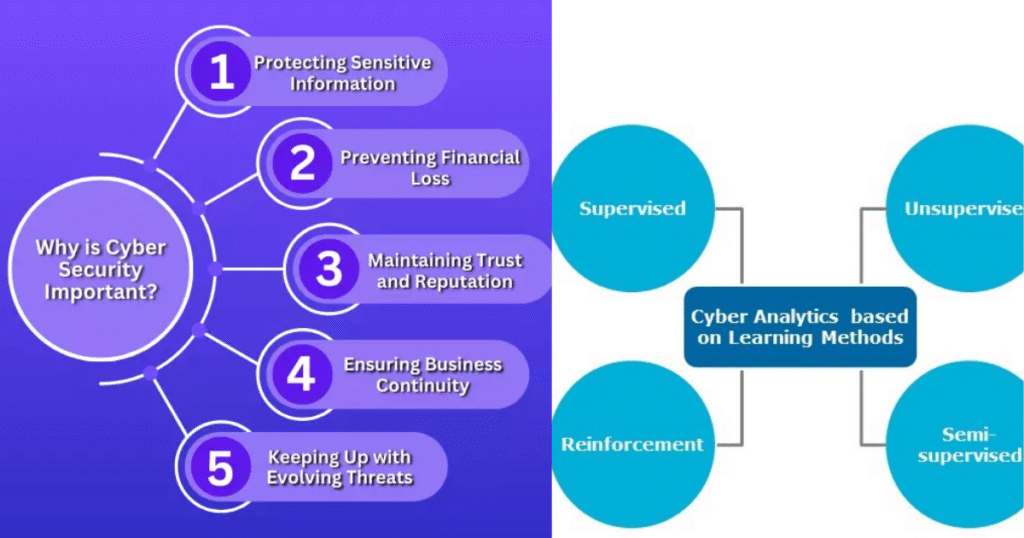
The importance of cybersecurity has grown with the upward thrust of superior technology which include self-using automobiles, internet-enabled domestic devices, and cloud-based services. Cyberattacks are not restrained to stealing data; they can disrupt operations, cause monetary loss, and damage an enterprise’s reputation. Stolen sensitive facts frequently end up on the dark web, wherein it’s far bought for fraudulent purposes. past the immediate monetary damage, a safety breach can result in criminal consequences, loss of customer consideration, and long-term harm to logo popularity. For smaller companies, those results may be deadly, as they’ll by no means absolutely get over the loss of clients and credibility.
Commonplace Cyber Threats You need to recognise

Cybercriminals use more than a few methods to make the most vulnerabilities, with phishing, ransomware, and social engineering being a few of the maximum common. Phishing hints victims into clicking malicious links or revealing non-public info, regularly through emails, textual content messages, or fake websites. Cybersecurity vs Information Security: Understanding the Differences and Defending Against Modern Threats Ransomware assaults involve encrypting an individual’s or organization’s information and disturbing a ransom to restore get admission to, but even payment does no longer assure information recovery. Social engineering is predicated on human manipulation—such as impersonating an IT help worker over the smartphone—to extract touchy statistics like passwords or security codes. These techniques target each technology and human behavior, making layered safety features critical for powerful protection.
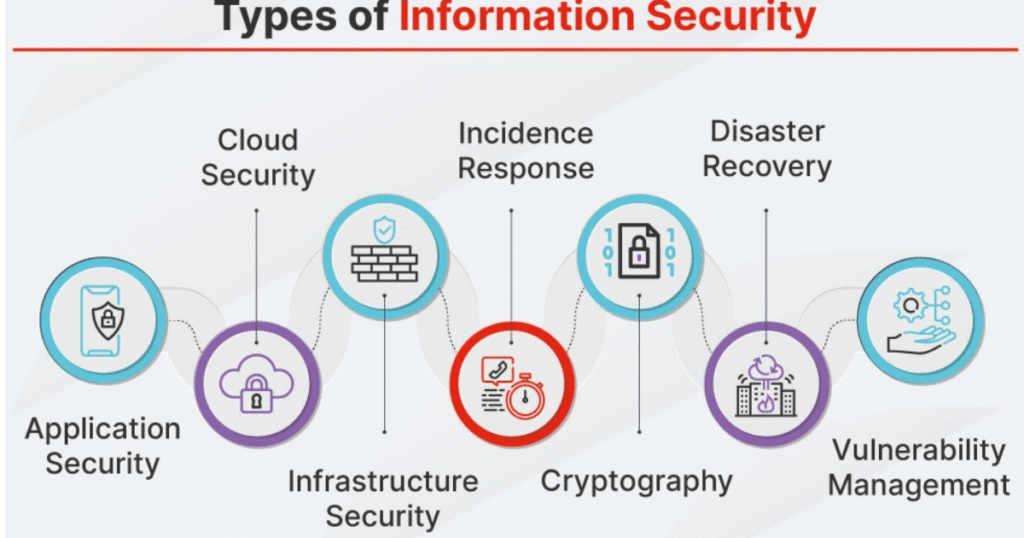
Key varieties of Cybersecurity Measures

To combat those threats, agencies use unique cybersecurity techniques, including cloud protection and infrastructure safety. Cloud security protects statistics, applications, and structures in cloud environments from unauthorized access and data loss. Infrastructure protection safeguards critical physical and cyber structures which are important to society, together with strength grids, transportation networks, and verbal exchange structures. A sturdy protection calls for regulations like strict consumer account control, actual-time tracking for suspicious pastime, and restricting entry to confidential information. Cybersecurity vs Information Security: Understanding the Differences and Defending Against Modern Threats Corporations need to use trusted software providers, hold structures updated each day to fight new malware, and preserve provider contracts for rapid hardware repairs. Many organizations also maintain spare crucial additives accessible to lessen downtime at some stage in technical screw ups.
Constructing a sturdy Cybersecurity Framework
A stable cybersecurity method is extra than simply antivirus software—it’s an entire framework combining technology, guidelines, and worker cognizance. Normal updates are critical to keep systems protected against evolving threats, at the same time as renovation contracts make certain short restoration from hardware issues. selecting an IT support organization with deep expertise of the agency’s hardware, software program, and community setup is crucial. Protection guidelines should encompass clear regulations for consumer control, incident reporting, and get right of entry to manipulate. Cybersecurity vs Information Security: Understanding the Differences and Defending Against Modern Threats Training employees is similarly crucial due to the fact human mistakes remain one of the leading causes of breaches. For those pursuing a profession in this area, a cybersecurity degree can provide the technical skills and strategic questioning vital to secure systems and manage organizational dangers. In the virtual era, cybersecurity isn’t always optional—it’s far a critical feature that protects operational balance, records integrity, and public consideration.
What is the main distinction among records protection and cybersecurity?
Statistics safety is the broader subject that protects all styles of statistics—digital and bodily—while cybersecurity focuses especially on safeguarding virtual systems, networks, and gadgets from cyberattacks.
Why has cybersecurity become extra critical in recent years?
With the growth of technologies like cloud computing, clever gadgets, and self-riding motors, cyber threats have increased appreciably. A single breach can reason economic loss, prison penalties, and severe reputational harm, mainly for small organizations.
What are 3 common types of cyberattacks?
The three most commonplace are phishing (tricking victims into revealing information or putting in malware), ransomware (encrypting information and demanding fee), and social engineering (manipulating human beings to proportion touchy information).
What are a few examples of cybersecurity measures?
Examples include cloud security, infrastructure safety, strict user account management, normal software program updates, relying on software program vendors, and keeping spare important components to reduce downtime for the duration of failures.
How can businesses reinforce their cybersecurity framework?
they could integrate generation, clear protection regulations, and worker schooling. Ordinary updates, sturdy incident detection structures, reliable IT aid, and right get admission to manage help ensure structures remain covered towards evolving threats.
conclusion
Cybersecurity and information protection are crucial for defensive records, retaining belief, and making sure agency continuity. In a technology of evolving threats like phishing, ransomware, and social engineering, organizations want to combine technology, strong guidelines, and worker interest to stay comfy.
Related Reads
- Custom Fitness App Development: Build the Fitness App Your Users Actually Want
- Roadrunner Email Account Login: A Complete Guide
- Top Lake Erie Fish Species and the Best Seasons to Catch Them
- Saudi Arabia Bioplastics Market Expansion, Share, Growth and Research Report 2025-2033
- Senior Construction Estimating Consultant
- How Often Should You Attend Fitness Group Training Sessions?



